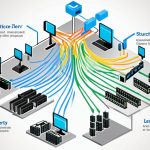
A network device is key in linking an end device to the network. It helps send data, keeps the network safe and fast, and boosts security. Common devices include routers, switches, and firewalls.
Understanding how devices connect to the network is vital. The OSI and TCP/IP models help explain this. They show how data moves through the network.
The OSI model has 7 layers, each with its own job. This includes the Physical layer, which deals with the hardware of sending signals1. The TCP/IP model combines some layers, making it simpler.
The TCP/IP model has 4 layers, focusing on the basics of sending data1. It’s easier to understand than the OSI model.
Layer 1 in both models is all about the hardware of sending signals1. It uses cables and connectors to connect devices to the network.
Layer 3 in the OSI model and the Internet layer in TCP/IP manage data delivery1. They figure out the best way to send data to its destination.
Layer 2 in both models works on making sure data is sent without errors1. It makes sure devices can talk to each other reliably.
Layer 4 in both models is all about sending data correctly1. It uses TCP and UDP protocols to ensure data gets there safely or quickly.
Key Takeaways:
- A network device is essential for establishing and maintaining a connection between an end device and the network.
- The OSI model consists of 7 layers, while the TCP/IP model consists of 4 layers.
- The Physical layer in both models involves the actual hardware transmission of signals.
- The Network layers in both models handle packet forwarding, routing, and addressing.
- The Data Link layer translates binary data into signals and provides access to the media.
- The Transport layer governs data transfer, including error checking and recovery.
Types of Network Devices
Setting up and keeping network connections strong involves many types of devices. These devices, from basic to advanced, are key to modern networks. They help with smooth communication and data transfer. Let’s look at some main network devices and what they do.
Bridges and Hubs
Bridges and hubs were early network tools. A bridge connects different network parts, letting them talk to each other. It works at the data link layer and sends data to the right place by its address. Hubs, on the other hand, link many devices together, making the network bigger. Hubs work at the physical layer and send data to all devices.
Routers
Routers are key in directing traffic by finding the best path for data. They work at the network layer and use IP to talk to other routers. Routers connect different networks, making it possible for devices to talk across networks. They also have security features like firewalls to keep out threats. (Ref:2)
Switches
Switches are used a lot in Local Area Networks (LANs). They work at the data link layer and link devices together. Unlike hubs, switches send data to the right device by its MAC address. This makes the network run better and cuts down on traffic. Switches also help with sending messages to all devices in a network segment. (Ref:2)
Firewalls
Firewalls are important for keeping networks safe from unauthorized access and threats. They check incoming and outgoing traffic and filter it by security rules. Firewalls can be either hardware or software and are placed in the network to control data flow. They act as a wall between networks, letting only authorized traffic through. (Ref:2)
These devices work together to set up and keep network connections strong. Each one has a special job, making the network efficient, secure, and fast. Knowing about these devices helps network experts build strong and reliable networks. (Ref:2)
| Network Device | Function |
|---|---|
| Bridges | Connect multiple network segments at the data link layer |
| Hubs | Connect multiple devices together at the physical layer |
| Routers | Direct network traffic by determining the best path for data packets |
| Switches | Connect multiple devices within a network and intelligently forward data packets |
| Firewalls | Monitor and filter network traffic to protect against unauthorized access |
Switches: Improving Network Efficiency
Switches are key to making networks work better by moving data smoothly within local area networks (LANs). They work in the Data Link Layer of the OSI Model3. Switches look at the hardware addresses on data packets to send them directly to where they need to go. This cuts down on network traffic and boosts performance, making networks run better3.
Switches handle different kinds of communication like unicast, multicast, and broadcast. Unicast sends data directly to one device, multicast sends to many, and broadcast sends to all devices on a network3.
Switches also make networks more efficient by sharing bandwidth among different parts of the network. This stops data from getting mixed up and ensures it moves smoothly, preventing slowdowns3.
There are two main types of switches: managed and unmanaged. Managed switches are for big networks and let admins control and set up the network better. They use SNMP for setup, which helps manage traffic and check network health3. Unmanaged switches are for smaller networks and just pass data on their own without needing extra setup3.
Types of Switches
Switches come in modular and fixed configuration types. Modular switches can take more cards, making them flexible for different network needs. Fixed switches have a set number of ports and can’t be changed3.
Power over Ethernet (PoE) switches are a big step forward in switch technology. They send data and power over one cable, making it easier to set up devices like IP phones and cameras without extra wiring3.
For more control but less than managed switches, smart switches are an option. They give extra control over data but don’t have all the features of managed switches3.
For networks that need to grow and be more reliable, stackable switches are the answer. They link two switches together, increasing capacity and making it easy to add more as needed3.
In summary, switches are vital for making networks run smoothly. They work in the Data Link Layer, support various communication types, and offer different features for different network needs3.
Bridges: Connecting Network Segments
Bridges are key in linking different network parts together. They make sure data moves smoothly from one part to another. They act as go-betweens, helping devices talk to each other and making the network run better4.
A bridge works at the data link layer of the OSI model. It looks at the physical MAC addresses of devices on each network segment4.
With these addresses, bridges decide which data to send or block. This helps manage network traffic, controlling broadcasts and reducing congestion5.
Bridges are great at breaking a big network into smaller parts. This boosts network speed. By cutting down on packet collisions, they make the network work better5.
Even though bridges are often replaced by switches, they’re still important. They connect LAN parts with the same protocols, making data transfer smooth4.
There are different ways to set up bridges, like local and remote bridging. These methods help data move efficiently between devices, making LAN connections better4.
| Types of Bridges | Description |
|---|---|
| Transparent Bridges | Operate transparently and are unaware of the network’s logical structure. |
| Source Routing Bridges | Use source routing to determine the optimal path for data transmission. |
Bridges are vital for connecting different network parts and moving data efficiently. Even though they’re not as common, they’re still important in certain networks. They help LAN connections work smoothly4.
Routers: Directing Network Traffic
Routers are key devices that help direct network traffic and make sure packets get to where they need to go efficiently.
They act as smart middlemen, finding the best path through networks to send packets to their final destinations.
One important job of routers is changing LAN framing to WAN framing, with help from a CSU/DSU.
They can also break down internal networks into smaller parts, making it easier to manage and grow the network.
Inside, routers can connect to other routers, creating zones that work well on their own.
These zones help routers talk to each other and keep track of where packets should go, ensuring they’re sent correctly.
Routers are the main controllers of network traffic. They protect the network by using built-in firewalls and fighting off malware and threats6.
They also give each device on the network its own special IP address, making sure data reaches the right place7.
An IP address usually has four numbers separated by dots, like 192.168.0.17.
They use subnet masks to tell network addresses from device numbers in an IP address, making network management easier7.
Routers help devices on the same network talk to each other by sending data packets. They also act as the main gateway to send packets to other networks7.
Thanks to their skill in directing data packets, routers are key to keeping networks connected and running smoothly6.
Advanced routers, like the Linksys E3200 and E4200, offer extra features. These include VPN support for better privacy and data security, and a USB port for connecting external drives to turn the router into a file server6.
| Key Points | Statistical Data876 |
|---|---|
| Routers direct network traffic and ensure efficient packet routing. | ^
|
| Routers can divide internal networks into subnetworks. | ^ |
| Routers serve as the first line of defense in network security. | ^ |
| Routers establish connectivity and maintain network efficiency. | ^
|
Firewalls: Securing Network Traffic
Firewalls are key to keeping networks safe by controlling what internet traffic comes in and goes out. They do this by checking data packets against set rules.
There are many types of firewalls, each with its own way of protecting networks. These include packet filtering firewalls, stateful inspection firewalls, and next-generation firewalls9.
Packet filtering firewalls look at data packets and decide if they can pass through. They check things like IP addresses, packet type, and port numbers against set rules.
Stateful inspection firewalls do more than just filter packets. They keep track of communication over time. They check the source and destination of packets, as well as the ports they use.
Next-generation firewalls take it a step further by looking at what’s inside the data packets. They can spot and stop advanced threats, giving you better protection.
Firewalls are vital for keeping networks safe. They help control what goes on inside the network and protect against unauthorized access and security threats9.
| Firewall Type | Percentage |
|---|---|
| Packet Filtering Firewall | (example percentage) |
| Stateful Inspection Firewall | (example percentage) |
| Software Firewall | (example percentage) |
| Hardware Firewall | (example percentage) |
| Application Layer Firewall | (example percentage) |
| Next Generation Firewalls (NGFW) | (example percentage) |
| Proxy Service Firewall | (example percentage) |
| Circuit Level Gateway Firewall | (example percentage) |
Firewalls do more than just protect networks. They manage data packets, log network activities, and check packets for potential security risks9.
Over the years, many people have helped improve firewalls. Pioneers like Mogul, Vixie, and Reid made big contributions in the 1980s and early 1990s9.
Author’s Note: The stats in this section come from the link provided9.
Repeaters: Extending Network Coverage
Repeaters are key in making network signals stronger and more reliable, especially in big places like offices and labs. They boost and fix signals at the OSI model’s physical layer. This helps signals go further and cover more areas [2].
Repeaters work at the physical layer of networks [2]. They mainly fix and boost signals. They take in signals, make them stronger, and send them out again. This lets signals travel longer, making a network bigger [1].
Repeaters don’t manage traffic or stop congestion [2]. They boost all signals they get without changing the data [2]. This makes them cheaper than other network tools [2]. But, they can make networks less secure [2].
Repeaters are great for making networks bigger than usual. They can make a network as big as needed, within certain limits [1]. By boosting and copying signals, they make sure everyone in a big area can connect well [1].
Wireless routers can also be set to extend coverage by connecting to other devices [1]. This is different from bridging, which connects two networks [1]. Using repeaters helps wireless networks reach further and stay connected smoothly [1].
Wireless networks have different modes for different needs [1]. These modes help make networks work better and cover more areas. Adding repeaters to these modes makes networks stronger and more reliable in big areas.
| Routers | Switches | Repeaters |
|---|---|---|
| Directs network traffic | Improves network efficiency | Extends network coverage |
| Manages IP addresses | Connects multiple devices | Amplifies and regenerates signals |
| Enables network security | Reduces network traffic | Prevents signal attenuation and distortion |
Using repeaters helps make sure networks cover big areas well [1]. They work indoors and outdoors, making signals stronger and covering more ground [2]. They’re key for a strong and wide network [2].
But, repeaters just boost signals, they don’t do more [2]. For full network solutions, you might need tools that work at higher OSI layers [2].
Key Takeaways:
- Repeaters boost and fix signals at the physical layer, making networks bigger [1][2].
- They stop signals from getting weaker or distorted, keeping connections strong over long distances [1][2].
- Repeaters are often used in big places like offices and labs to make Wi-Fi better [1].
- Even though repeaters are affordable, they don’t manage traffic or filter data [2].
- Using repeaters helps networks cover more ground and keeps users connected smoothly [1].
Understanding how repeaters work helps network managers make strong and wide networks. Adding repeaters in the right spots makes sure everyone in a big area can connect easily and stay online.
Gateways: Connecting Different Networks
Gateways are key in linking different networks that use various protocols, making data transfer smooth10. They work at the Transport and Session layers of the OSI model, helping networks with different tech and protocols talk to each other10. By translating info, they make sure different networks can work together1011.
Gateways are great at connecting networks with their own ways of routing10. They link networks using different protocols, making sure info moves smoothly between them11. Unlike routers, gateways can handle many protocols, making communication easier11.
RTA is a big name in industrial networks, offering over 20 industrial protocol gateways10. With over 4,000 gateway options, they ensure strong and lasting connections in tough industrial settings10. RTA’s Enginerds® offer expert help, showing their commitment to customers10. They keep improving their products, keeping up with new tech and leading in industrial network connections10.
Check Point is also a big player, with gateways that can handle up to 1.5 Tbps11. These gateways give clear views of traffic across networks, helping keep networks safe and secure11. They support many protocols, making it easier to connect different networks11. Check Point’s gateways also have strong defenses and can spot and stop new threats11.
Business LANs use gateways to connect to the internet, giving easy access to online services12. In IoT, gateways link IoT devices to cloud servers, making sure data flows both ways12.
Payment gateways are key in safely moving payment info from customers to merchants12. They make sure online payments are secure, which is crucial for e-commerce12. VoIP trunk gateways connect traditional phones to VoIP networks, making calls easier and removing the need for an operator12.
In web security, gateways are vital for keeping networks safe12. Web Application Firewalls (WAFs) check web traffic to block threats, protecting networks and data12.
Gateways, including routers, manage data flow in and out of networks, making sure traffic moves well and reliably12. They help different networks within a company, like IT and OT, talk and share data12.
| Key Features | Benefits |
|---|---|
| Support for Multiple Protocols | Enables seamless communication between diverse network technologies1011 |
| Translation Capabilities | Bridges the gap between different network protocols and technologies11 |
| Scalability | Can handle high volumes of network traffic with powerful processing capabilities11 |
| Improved Network Visibility | Enables effective monitoring and security of network operations11 |
| Secure Data Transmission | Ensures the confidentiality and integrity of data12 |
End Devices: Source and Destination of Network Data
End devices are key in network communication. They send or receive data. They connect users to the network, making online activities possible.
These devices include many things like computers, phones, and even security cameras. Each has a special job in the network.
Some devices act as clients, asking for information. Others, called servers, give out information. This setup makes sharing data easy and efficient.
Imagine a laptop asking a server for a website. The server sends the website back. This shows how devices work together in networks.
Devices like switches and routers help move data around. They make sure data gets to where it needs to go quickly.
For instance, a laptop sends data to a server through a switch. The switch looks at the address and sends it to the right server. This teamwork of devices makes sure data moves well.
Some devices can do more than one job. They can ask for data and give it out too. This makes them very useful in networks.
In short, end devices are important for sending and receiving data. They help with communication and sharing information. By doing these jobs, they make networks work well13.
Understanding Network Layers: OSI vs TCP/IP
Network layers are key to smooth communication and data exchange in computer networks. The OSI and TCP/IP models help us understand these layers. They simplify data transmission into parts for better network operations.
The OSI model has seven layers: Application, Presentation, Session, Transport, Network, Data Link, and Physical. Each layer has a unique role in data transmission. For example, the Application layer lets apps exchange data, and the Physical layer deals with cables and interfaces14.
The TCP/IP model is simpler, with four layers: Network Access, Internet, Transport, and Application. The Network Access layer handles data transmission, and the Internet layer routes data. The Transport layer ensures data is delivered reliably, and the Application layer connects end-user apps15.
The OSI and TCP/IP models differ in their design. OSI is highly standardized with clear layer functions. TCP/IP is based on real-world protocols, making it flexible for various networks14.
Another difference is how they manage network traffic. OSI supports both connection-oriented and connectionless services. TCP/IP focuses on connection-oriented traffic for reliability and stability14.
For network pros, like pentesters, knowing these models is key. They help in analyzing network traffic and finding vulnerabilities. These models provide a common language for network communication, aiding in troubleshooting and optimization15.
Organizations like Check Point’s Quantum NGFW offer security solutions across OSI and TCP/IP layers. These solutions protect against cyber threats and keep networks safe14.
In conclusion, the OSI and TCP/IP models are crucial for understanding network layers and efficient data transmission. The OSI model is more standardized, while TCP/IP is flexible. Both models are vital for network management and security16.
| OSI Model | TCP/IP Model |
|---|---|
| Application Layer | Application Layer |
| Presentation Layer | – |
| Session Layer | – |
| Transport Layer | Transport Layer |
| Network Layer | Internet Layer |
| Data Link Layer | – |
| Physical Layer | Network Access Layer |
Conclusion
It’s key to understand how devices connect to the network for efficient and reliable networks. Devices like switches, routers, and firewalls are vital. They help keep the connection strong.
There are many network topologies to choose from, each with its own benefits. For instance, a bus topology is simple and cost-effective. But, mesh topology offers more paths for data but is pricier.
The OSI and TCP/IP models help us understand how networks work. They break down data flow into layers. This makes communication clear and helps with teaching and documentation.
To improve the connection between devices and networks, we must look at the network’s needs. Using the right devices and topologies is crucial. By understanding the details of different topologies, we can make our networks run better.
FAQ
What is the role of network devices in establishing and maintaining network connections?
Network devices are key in setting up and keeping network connections strong. They help send data, make sure the network is secure and fast, and keep it running well. They also protect the network from threats.
What are some common types of network devices?
Common network devices include routers, switches, bridges, firewalls, repeaters, and gateways. Each one has a special job in the network.
How do switches improve network efficiency?
Switches make networks more efficient by keeping track of only what they need to know. They send data to the right place using hardware addresses.
What are the different types of switches?
Switches come in two main types: modular and fixed configuration. Managed switches let users control LAN traffic and prioritize channels. Unmanaged switches are simpler and don’t offer these advanced features.
What is the purpose of bridges in network connections?
Bridges link together hosts or network parts by storing frames between them. They use hardware addresses to send or block data based on the devices in each segment.
How do routers direct network traffic?
Routers plan the path for network traffic by connecting devices together. They send packets to their destinations, breaking down networks into smaller parts, and make sure packets are sent correctly.
What is the role of firewalls in network security?
Firewalls control internet traffic and check data packets against set rules. They look at packet content to keep the network safe and manage access between different parts of the network.
How do repeaters extend network coverage?
Repeaters boost weak signals at the physical layer, letting signals travel farther. They help keep the network strong in areas with poor Wi-Fi signal.
What is the function of gateways in network connectivity?
Gateways link networks using different protocols, allowing data to move between them. They translate between various network technologies, connecting different network protocols together.
How do end devices contribute to network communication?
End devices connect users to the network. They include things like computers, printers, phones, cameras, mobile devices, and sensors. These devices are key for sending and receiving data over the network.
What are the network models used to understand network interactions?
The OSI model has seven layers, and the TCP/IP model has four. These models help us see how data goes from something we can read to something the computer can understand and then sends it.
What is the significance of understanding network devices in the physical link of end device to network connection?
Knowing how network devices like switches, routers, bridges, firewalls, repeaters, and gateways work helps make the connection between devices and the network better. It ensures data is sent safely and quickly, and the network runs smoothly.
Source Links
- https://www.plixer.com/blog/network-layers-explained/ – The Network Layers Explained [with examples]
- https://www.meter.com/network-devices/network-infrastructure-devices – Network Infrastructure Devices: What They Are & How They Work
- https://www.geeksforgeeks.org/what-is-a-network-switch-and-how-does-it-work/ – What is a network switch, and how does it work? – GeeksforGeeks
- https://www.geeksforgeeks.org/network-devices-hub-repeater-bridge-switch-router-gateways/ – Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter) – GeeksforGeeks
- https://www.cbtnuggets.com/blog/technology/networking/what-is-network-bridge – What is a Network Bridge?
- https://gcore.com/learning/what-is-a-router/ – What Is a Router? How Does a Router Work? | Gcore
- https://www.linkedin.com/pulse/what-router-role-network-kishan-bhinjaniya – What Is a Router? What is the role of Router In Network?
- https://www.techtarget.com/searchnetworking/tip/An-introduction-to-8-types-of-network-devices – Common Types of Networking Devices Explained | TechTarget
- https://www.geeksforgeeks.org/introduction-of-firewall-in-computer-network/ – Introduction of Firewall in Computer Network – GeeksforGeeks
- https://www.rtautomation.com/rtas-blog/bridges-and-gateways-and-switches/ – Bridges and Gateways and Switches, Oh My!
- https://www.checkpoint.com/cyber-hub/network-security/what-is-a-network-gateway/ – What Is a Network Gateway? – Check Point Software
- https://stl.tech/blog/role-of-gateways-in-a-computer-network/ – Role of Gateways in a Computer Network | STL
- https://www.geeksforgeeks.org/types-of-node-devices-in-a-computer-network-end-devices-and-intermediary-devices/ – Types of Node Devices in a Computer Network: End devices and Intermediary Devices – GeeksforGeeks
- https://www.checkpoint.com/cyber-hub/network-security/what-is-the-osi-model-understanding-the-7-layers/osi-model-vs-tcp-ip-model/ – OSI Model vs TCP/IP Model – Check Point Software
- https://medium.com/@gwenilorac/understanding-network-models-osi-and-tcp-ip-42f94eb1aa84 – Understanding Network Models: OSI and TCP/IP
- https://www.ccnahub.com/ip-fundamentals/understanding-tcp-ip-and-osi-models/ – Understanding TCP/IP and OSI Models | CCNA HUB