Protocol Architecture in Computer Networks: What You Need to Know
Computer networks are vital for modern digital communication. They enable smooth data transmission across global systems. Network protocols act as a crucial language, setting rules for effective device communication.
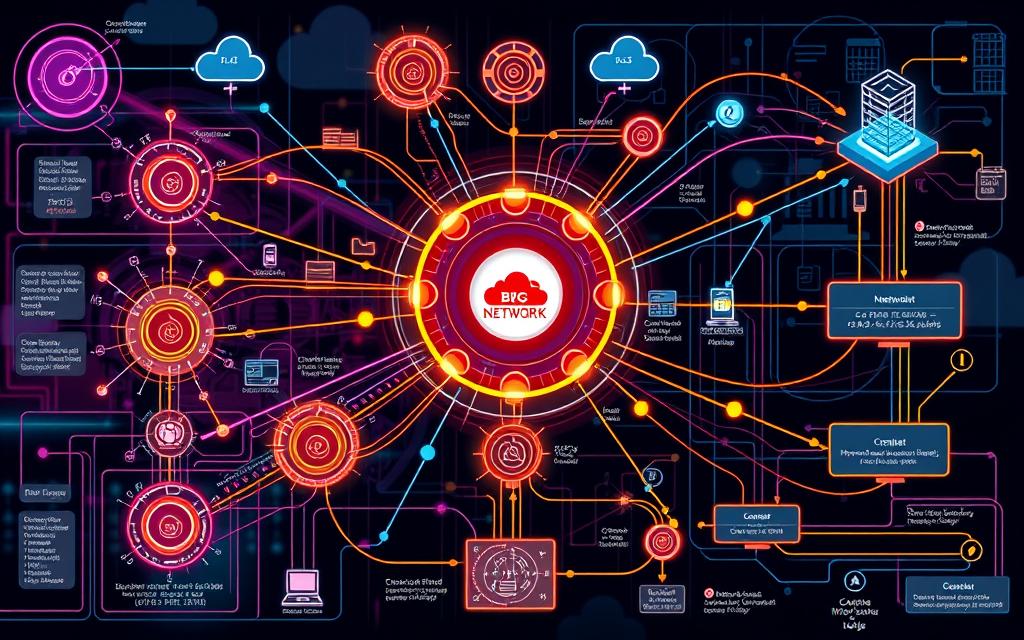
Protocol architecture is at the heart of network communication. It defines how services, devices, and clients interact. These systems ensure reliable and secure data transmission in complex digital ecosystems.
Network protocols are the foundation of computer networks. They create standard frameworks for data communication. These protocols allow different tech systems to work together seamlessly.
Network protocols play a crucial role in digital communication. They manage data packet routing, error detection, and flow control. They also handle security authentication in computer networks.
Protocol architecture reveals how modern digital systems communicate. It shows how they interact and maintain integrity. Protocol standards ensure smooth data transmission in both small and large networks.
Understanding Protocol Architecture Fundamentals
Protocol architecture is vital for smooth computer network communication. It allows diverse devices to exchange information efficiently and securely. This sophisticated system forms the backbone of modern digital interactions.
https://www.youtube.com/watch?v=RL29Ek77kYA
Network layers are crucial in structuring data transmission across digital environments. The protocol stack manages these complex communication processes systematically. It ensures data flows seamlessly between different network components.
Key Components of Protocol Architecture
The architecture of network protocols includes several essential elements:
- Hardware infrastructure (routers, switches, servers)
- Software protocols controlling data exchange
- Standardised communication interfaces
- Security mechanisms
Purpose and Importance in Network Communication
The OSI model is a comprehensive framework for understanding network interactions. Its primary functions include:
- Facilitating structured data transmission
- Enabling interoperability between different systems
- Providing a modular approach to network design
“Effective protocol architecture transforms complex technological interactions into seamless digital communication.”
Basic Elements of Network Protocols
Critical network protocols like TCP/IP form the backbone of modern digital communication. These protocols manage various aspects of data transmission across different network layers.
| Protocol Layer | Primary Function | Key Characteristics |
|---|---|---|
| Application Layer | User interface interactions | Supports HTTP, SMTP, FTP |
| Transport Layer | Reliable data delivery | Uses TCP/UDP protocols |
| Network Layer | Packet routing | IP address management |
Grasping these fundamental components is crucial for building robust network architectures. It helps organisations create scalable systems that support seamless digital communication. This knowledge is essential for designing efficient and reliable networks.
What is Protocol Architecture in Computer Network
Protocol architecture is the blueprint for network communication. It defines how digital systems exchange information efficiently and securely. This layered structure guides data transmission across complex computer networks.
It manages intricate data exchange through systematically designed layers. Each layer performs specific functions, ensuring seamless communication between network devices.
Structure and Layers of Protocol Architecture
Protocol architecture consists of multiple interconnected layers. Each layer handles distinct aspects of network communication. The most notable models include:
- TCP/IP protocol suite (five layers)
- OSI reference model (seven layers)
- Distributed network communication layers
Protocol Architecture vs Network Architecture
Protocol architecture focuses on communication rules and data transmission standards. Network architecture, however, deals with physical and logical network design. The two concepts are often confused but are quite different.
Role in Data Transmission
Protocol architecture ensures reliable and efficient data exchange. It manages critical processes such as:
- Data formatting
- Addressing mechanisms
- Transmission protocols
- Reception validation
“Protocol architecture is the invisible framework that enables seamless digital communication across global networks.”
| Protocol Layer | Primary Function | Key Protocols |
|---|---|---|
| Application Layer | User interface and service interactions | HTTP, FTP, SMTP |
| Transport Layer | End-to-end communication | TCP, UDP |
| Network Layer | Packet routing and addressing | IP, ICMP |
Protocol architecture is vital for network professionals. It helps design robust, scalable communication systems. These systems support modern digital infrastructure effectively.
Types of Network Protocols and Standards
Network protocols are the communication language for digital interactions. They enable smooth data transmission across complex technological ecosystems. These rules help diverse network devices interact, ensuring reliable and secure data exchange.
Network protocols support modern digital communications in several key categories:
- Communication Protocols (TCP/IP, HTTP, FTP)
- Network Management Protocols (SNMP, DHCP)
- Security Protocols (SSH, HTTPS)
Key network protocols have specific roles in digital infrastructure:
| Protocol | Primary Function | Usage Percentage |
|---|---|---|
| HTTP/HTTPS | Web Page Transfer | 90% of Web Traffic |
| TCP/IP | Reliable Data Transmission | 90% of Internet Traffic |
| SMTP | Email Communication | Global Email Routing |
| DNS | Domain Name Resolution | Internet Addressing |
Groups like IETF, IEEE, and ISO develop and maintain these protocols. They ensure interoperability and security across global network infrastructures.
Network protocols are the invisible languages that enable our interconnected digital world to communicate seamlessly.
Network protocols continue to drive technological innovation. They support emerging technologies like cloud computing, IoT, and intelligent automation systems.
OSI Reference Model in Protocol Architecture
The Open Systems Interconnection (OSI) Reference Model is crucial for grasping network communications. It divides complex network interactions into seven layers. This enables smooth data transmission across different computing systems.
The model helps professionals understand data encapsulation and protocol stack interactions. Each layer plays a vital role in successful data transmission.
https://www.youtube.com/watch?v=M1rj61txJJQ
Seven Layers of OSI Model
- Physical Layer: Handles raw bit transmission through physical media
- Data Link Layer: Ensures error-free node-to-node communication
- Network Layer: Manages packet routing across networks
- Transport Layer: Provides end-to-end data delivery
- Session Layer: Manages connections between devices
- Presentation Layer: Transforms data for transmission
- Application Layer: Interfaces directly with user applications
Layer Interactions and Functions
The protocol stack allows adjacent layers to interact smoothly. This enables complex data communication. As data moves through layers, each adds its header during transmission.
This process is called data encapsulation. It’s crucial for effective network communication.
Protocol Implementation Across Layers
| Layer | Key Protocols | Primary Function |
|---|---|---|
| Physical | Ethernet, Wi-Fi | Signal transmission |
| Network | IP, ICMP | Packet routing |
| Transport | TCP, UDP | End-to-end communication |
| Application | HTTP, FTP, SMTP | User interface services |
“The OSI model provides a universal language for understanding network communication.” – Network Engineering Experts
Network Security and Protocol Compliance
Cybersecurity is vital for organisations in today’s digital world. Network security protocols are crucial for safeguarding digital assets against cyber threats.
Authentication mechanisms are key to secure network communications. Organisations use robust access control strategies to reduce vulnerabilities.
Key approaches include:
- Multi-factor authentication systems
- Encryption technologies
- Comprehensive vulnerability management frameworks
Encryption is essential for network security. It turns sensitive data into unreadable formats for unauthorised parties. Many organisations use advanced cryptographic techniques to protect critical information.
“Security is not a product, but a process.” – Bruce Schneier
Effective vulnerability management needs ongoing monitoring and risk assessment. Companies must create strategies that include:
- Regular security assessments
- Penetration testing
- Systematic patch management
| Security Protocol | Primary Function | Protection Level |
|---|---|---|
| SSL/TLS | Encryption | High |
| IPsec | Network Layer Security | Very High |
| Kerberos | Authentication | Medium |
Using comprehensive network security protocols helps organisations reduce cyber risks. This approach protects their digital infrastructure from potential threats.
Protocol Architecture Implementation and Design
Effective network infrastructure design requires careful consideration of hardware and software components. Network configuration management ensures seamless communication and optimal performance. It’s crucial for maintaining a robust system.
Successful protocol architecture implementation involves integrating various network devices. It requires understanding the intricate protocol stack that enables data transmission. This knowledge is essential for creating efficient networks.
Essential Hardware Components
Key hardware elements form the backbone of network infrastructure:
- Routers for interconnecting network segments
- Switches for efficient data packet routing
- Servers hosting critical network services
- Firewalls providing security protection
Software Elements and Protocol Stack
The software ecosystem comprises protocols and applications that facilitate network topology and communication. Each protocol layer performs specific functions. These layers enable complex data exchanges while maintaining system integrity.
Network Configuration Best Practices
Implementing robust network configurations requires strategic planning:
- Configure routing protocols accurately
- Establish comprehensive firewall rules
- Implement virtual LAN segmentation
- Conduct regular security audits
A well-designed network architecture balances performance, security, and scalability.
Continuous monitoring keeps your network resilient. Periodic updates ensure it adapts to evolving technological challenges. These practices are vital for maintaining a secure network.
Conclusion
Protocol architecture is crucial for modern digital infrastructure. It enables sophisticated data communication across global networks. As technology advances, network efficiency becomes increasingly important for connecting diverse systems.
The significance of protocols cannot be overstated. By 2025, IoT devices are expected to reach 30 billion. Robust communication protocols will be vital for managing complex network interactions.
These protocols support everything from email transmissions to cloud computing environments. They provide the underlying framework for our digital world.
Network professionals must stay adaptable and knowledgeable about protocol standards. 40% of network management experts find protocol complexities challenging. This highlights the need for ongoing education in this ever-changing field.
Communication protocols will continue to drive innovation across various technological domains. They ensure secure, efficient, and reliable data exchanges in our interconnected world.
The ongoing evolution of these protocols promises exciting developments. We can expect advancements in network architecture and digital communication in the future.
FAQ
What is protocol architecture in computer networks?
Protocol architecture forms the backbone of network communication. It outlines how devices, services, and clients interact across different network layers. This framework sets rules for sending, receiving, and managing data transmission.
How do network protocols ensure secure data transmission?
Network protocols use various methods to safeguard data transmission. These include encryption, authentication protocols, and access control. They also implement error control and security measures at different network layers.
What are the key components of the OSI Reference Model?
The OSI Reference Model comprises seven distinct layers. These are Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer performs specific tasks to enable smooth data communication between devices.
What is the difference between protocol architecture and network architecture?
Protocol architecture focuses on rules for data communication. It defines how data is formatted, addressed, and transmitted. Network architecture, however, deals with the physical and logical design of network infrastructure.
Which are the most important network protocols?
Key network protocols include TCP, IP, HTTP/HTTPS, FTP, and SMTP. Others are DNS, DHCP, SSH, and SNMP. These protocols manage various aspects of network communication, from data transmission to device management.
How does data encapsulation work in protocol architecture?
Data encapsulation occurs as information moves through network layers. Each layer adds its own header to the data. When received, layers strip off their headers before passing data upwards.
Why is protocol compliance important in network security?
Protocol compliance ensures devices can work together smoothly. It establishes a security baseline and helps manage vulnerabilities. This approach helps organisations maintain robust networks by implementing standard communication rules.
What hardware components are crucial in protocol architecture?
Critical hardware components include routers, switches, servers, and firewalls. These devices manage data routing and network segmentation. They also control access and maintain overall network performance.
How do network protocols support different types of communication?
Network protocols provide specific rules for various data transmission needs. TCP ensures reliable data transmission for most internet traffic. UDP supports faster, connectionless communication for time-sensitive applications like online gaming.
What are the challenges in implementing modern protocol architecture?
Modern protocol architecture faces several challenges. These include managing complex networks and ensuring device compatibility. Maintaining robust security and handling high-speed data transmission are also key concerns.
Adapting to emerging technologies like IoT and 5G networks presents additional challenges. These new systems require innovative approaches to protocol architecture.